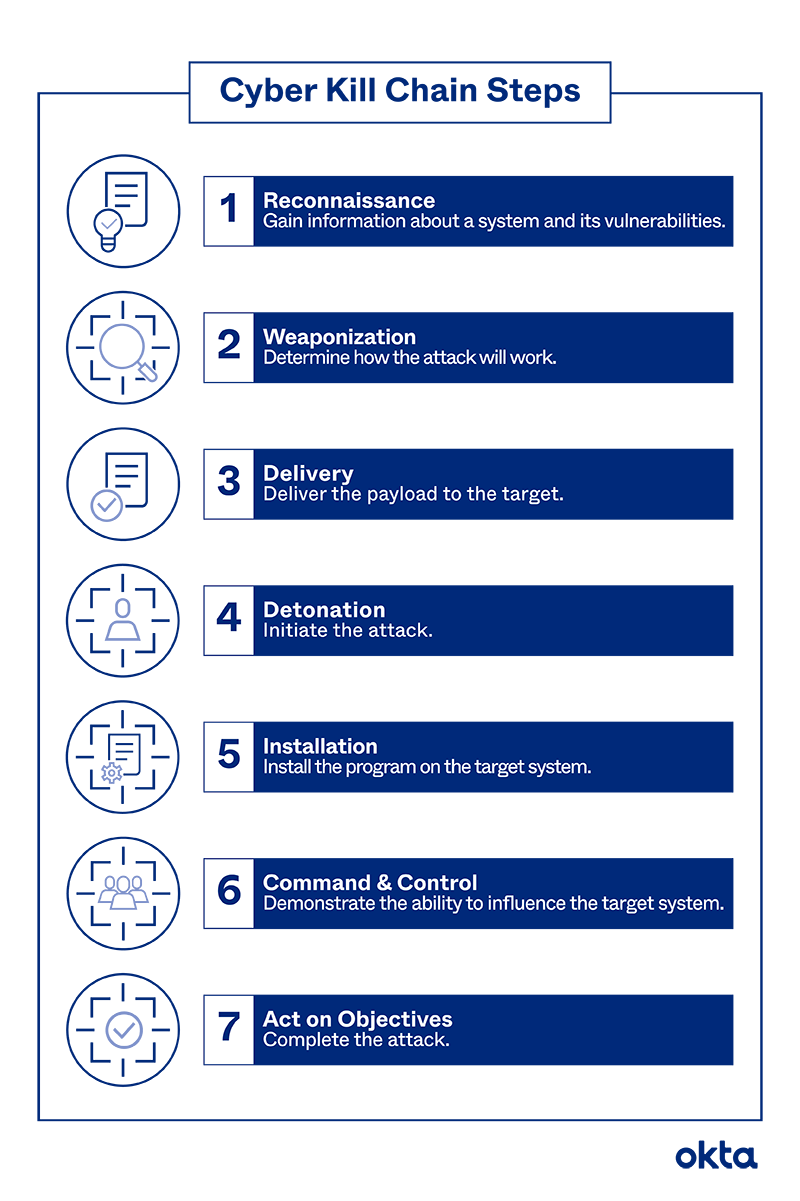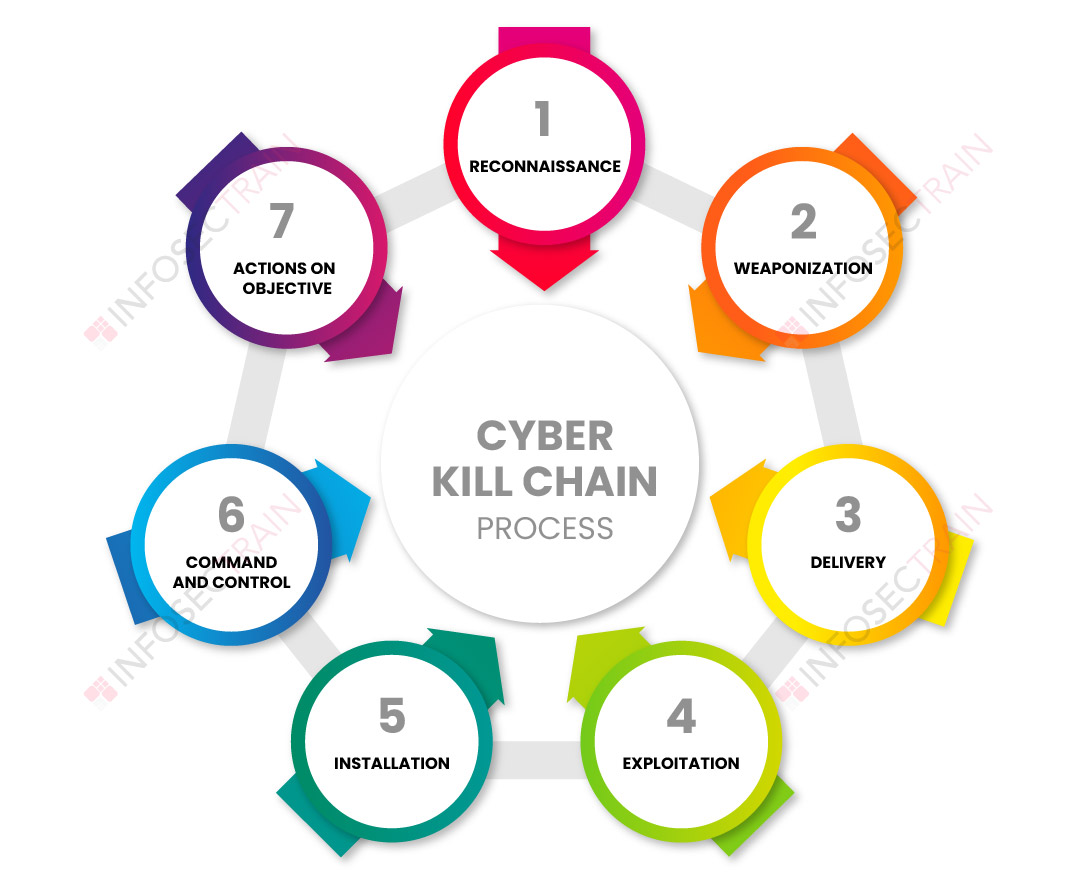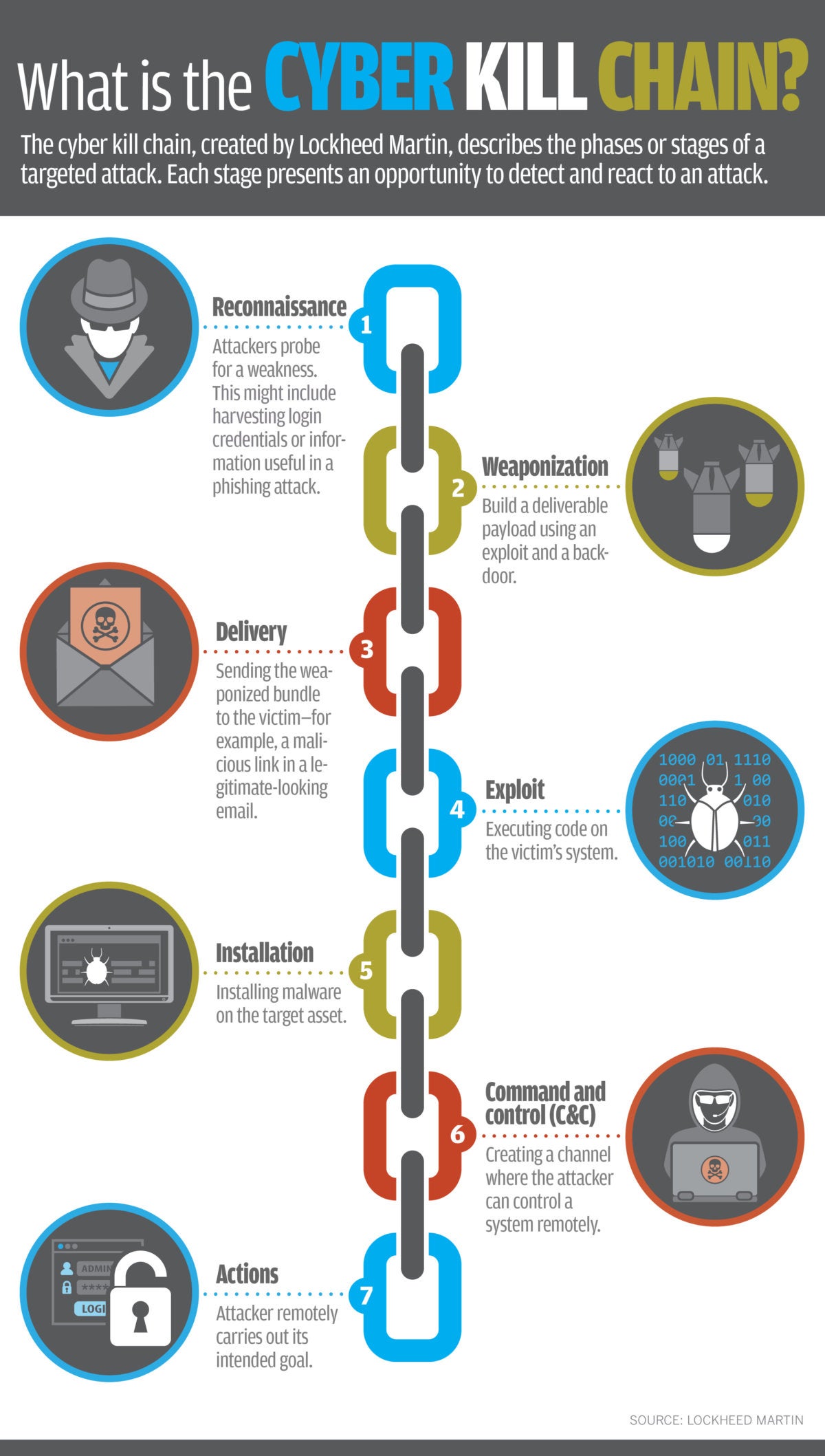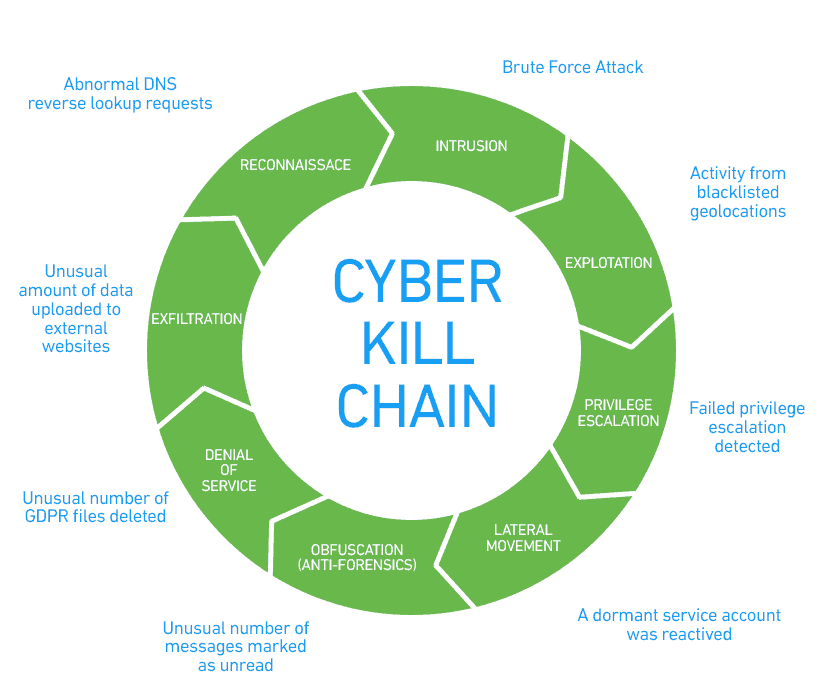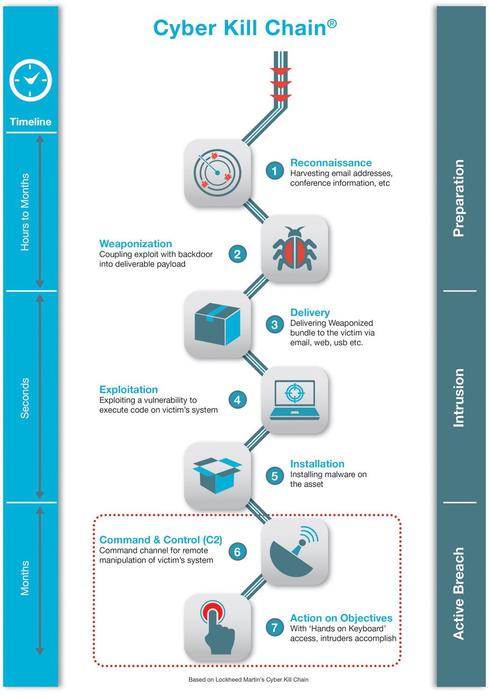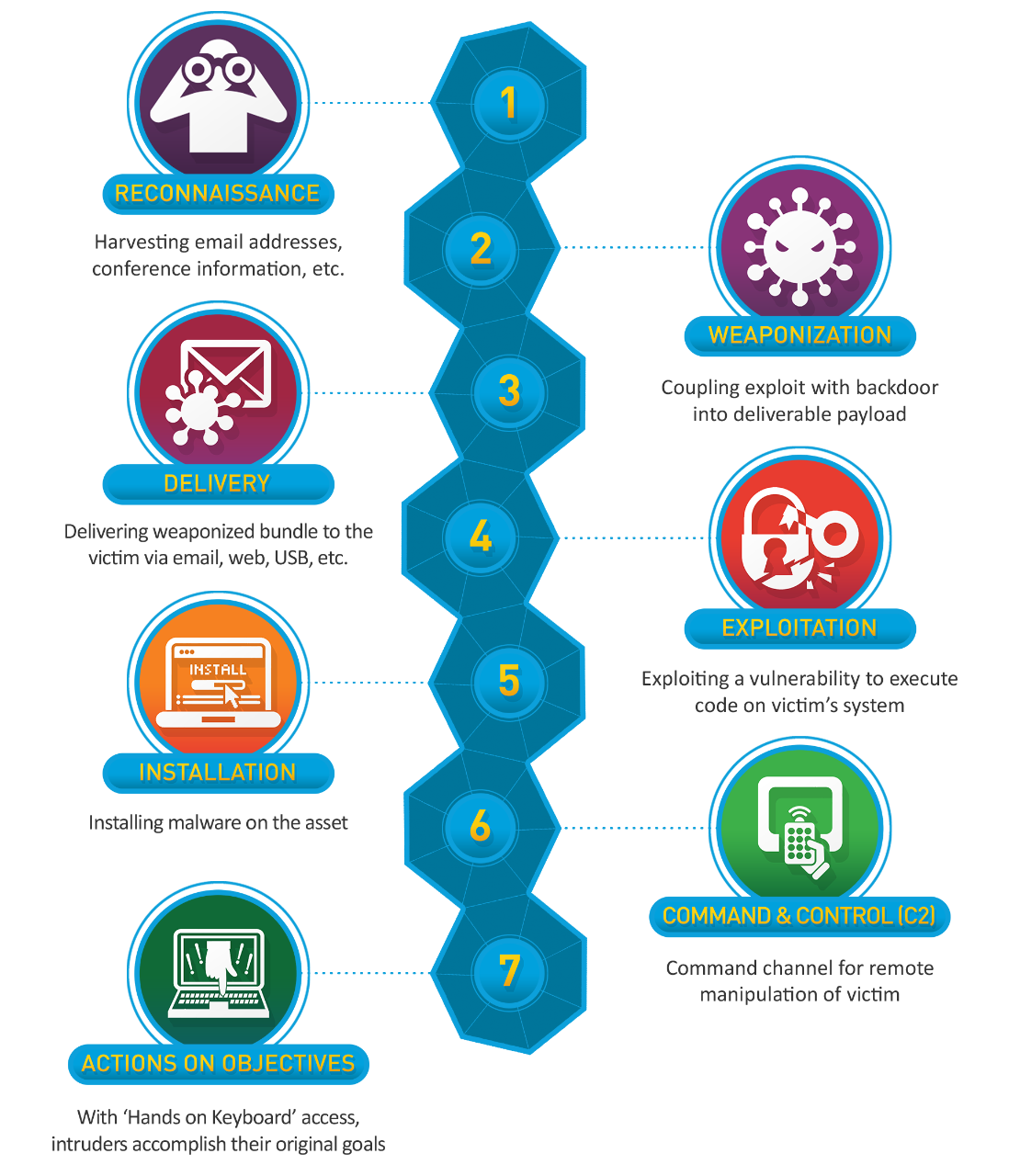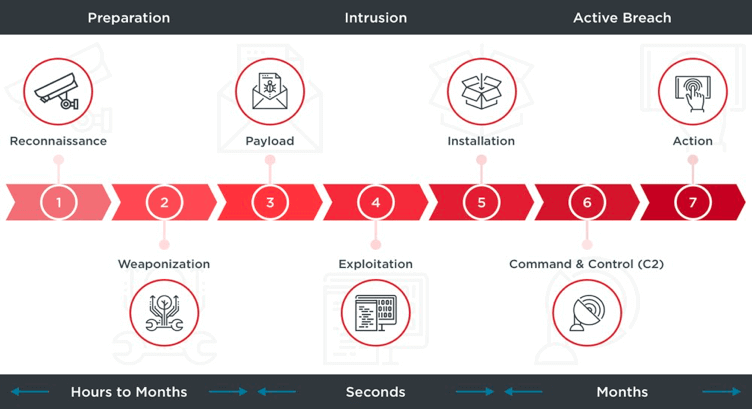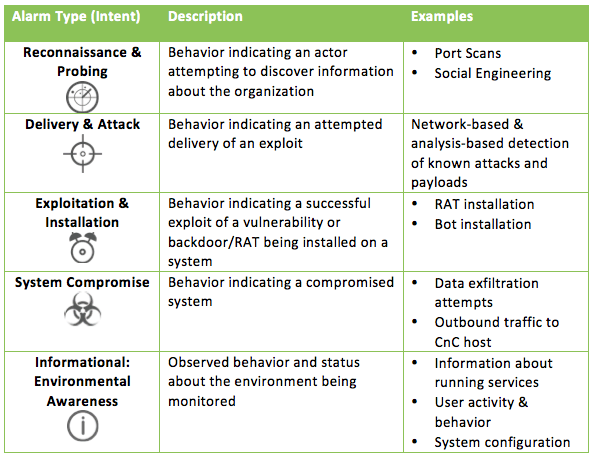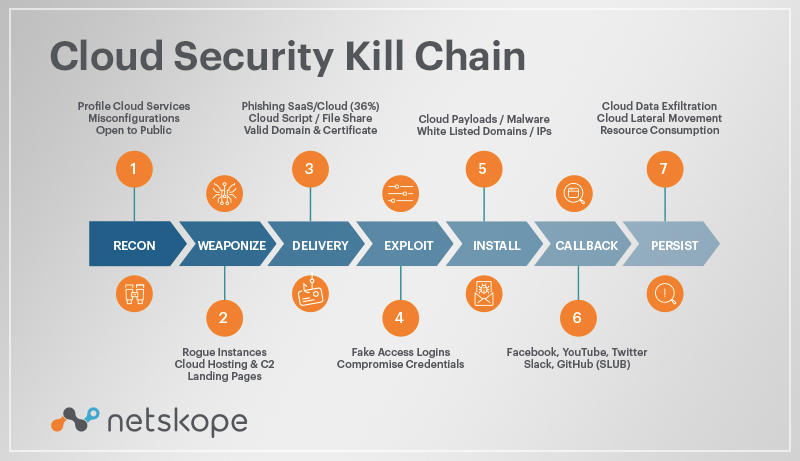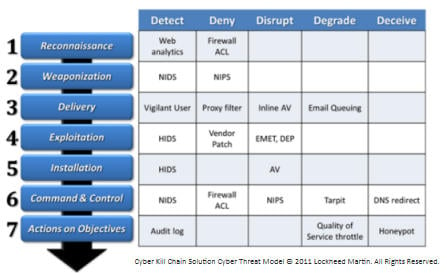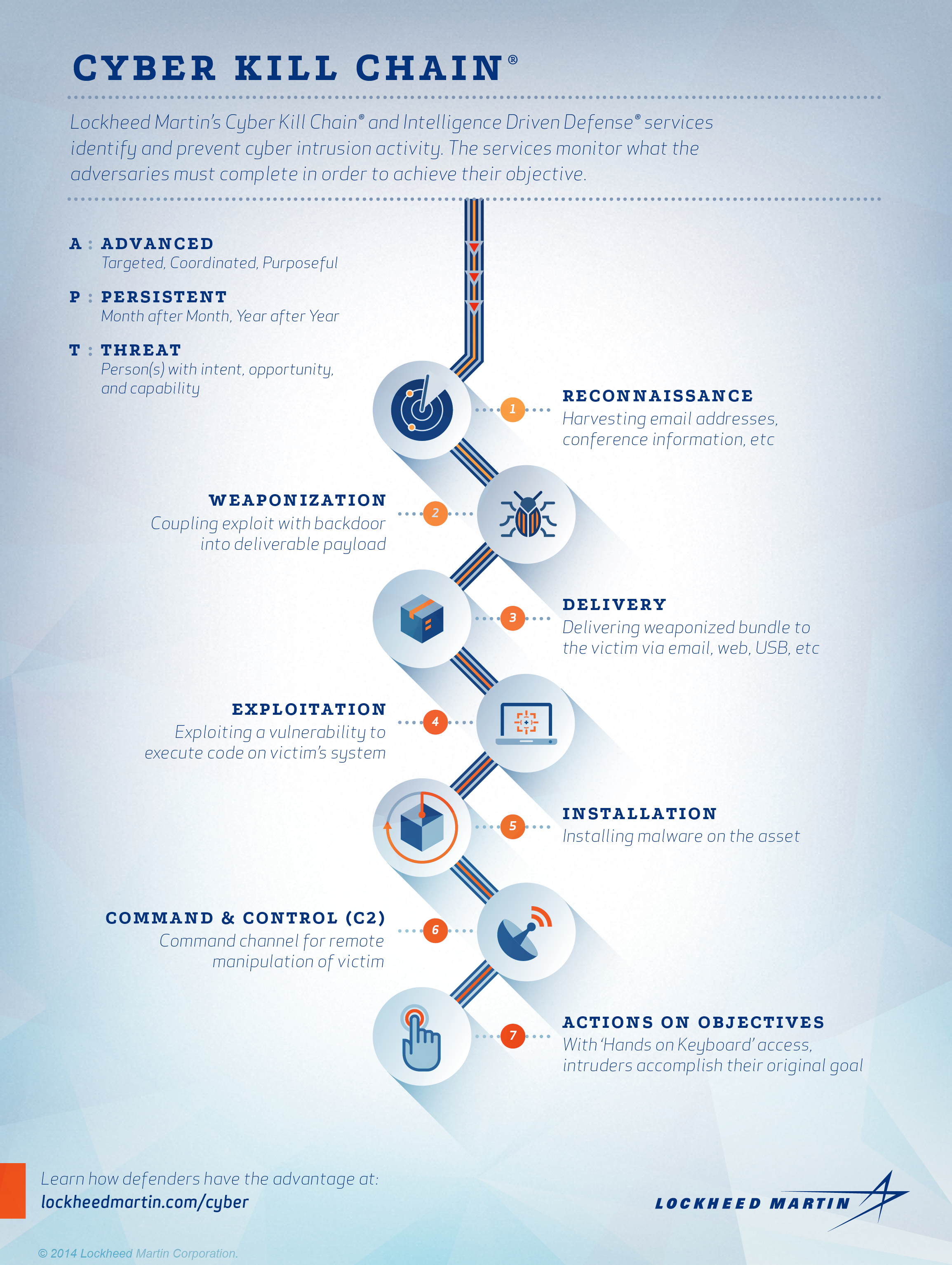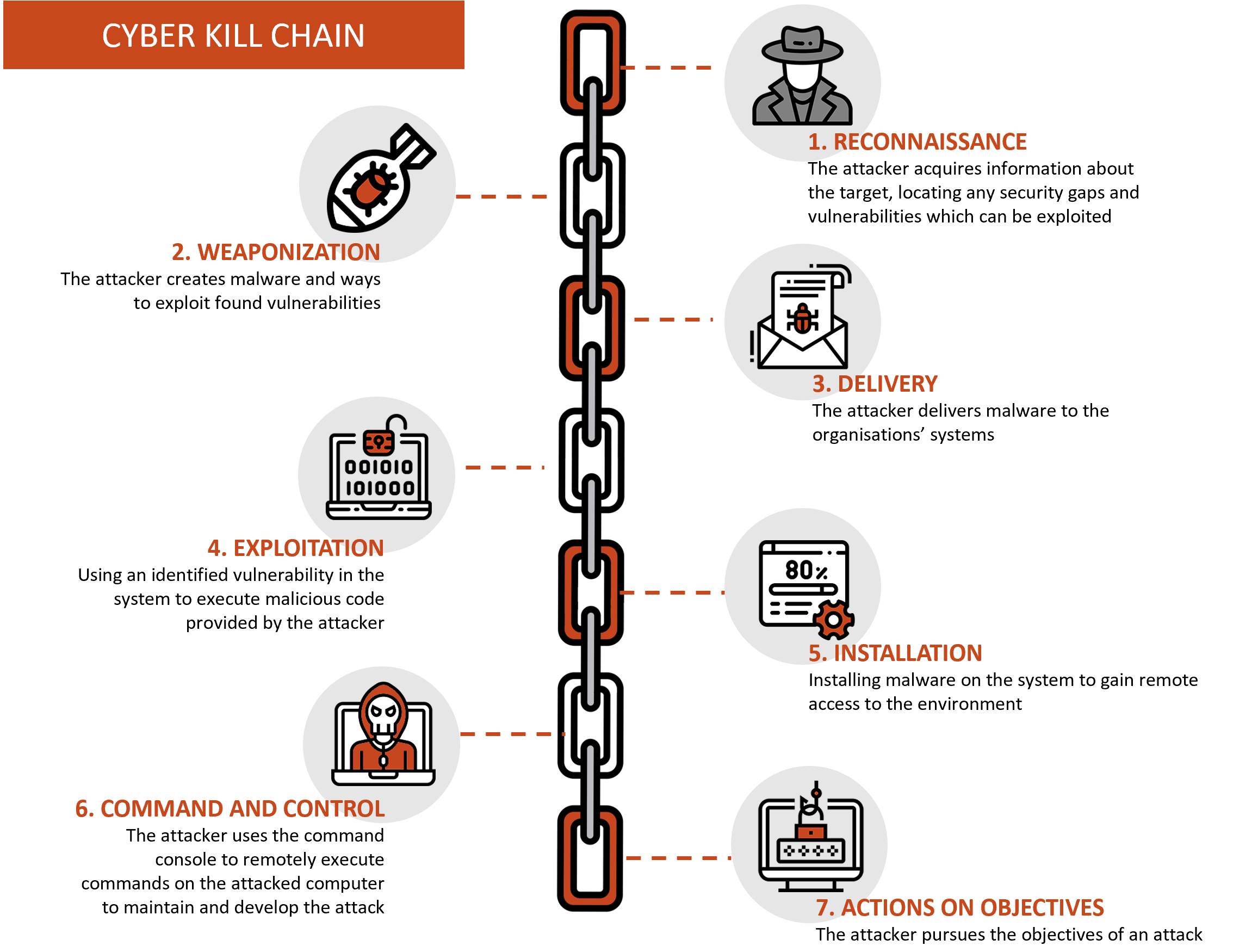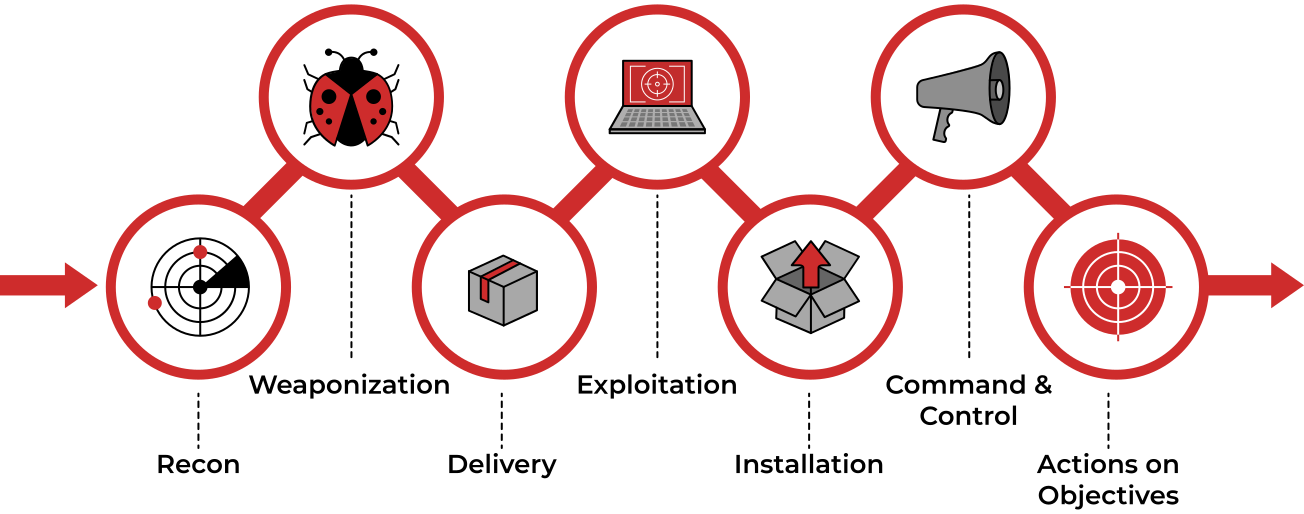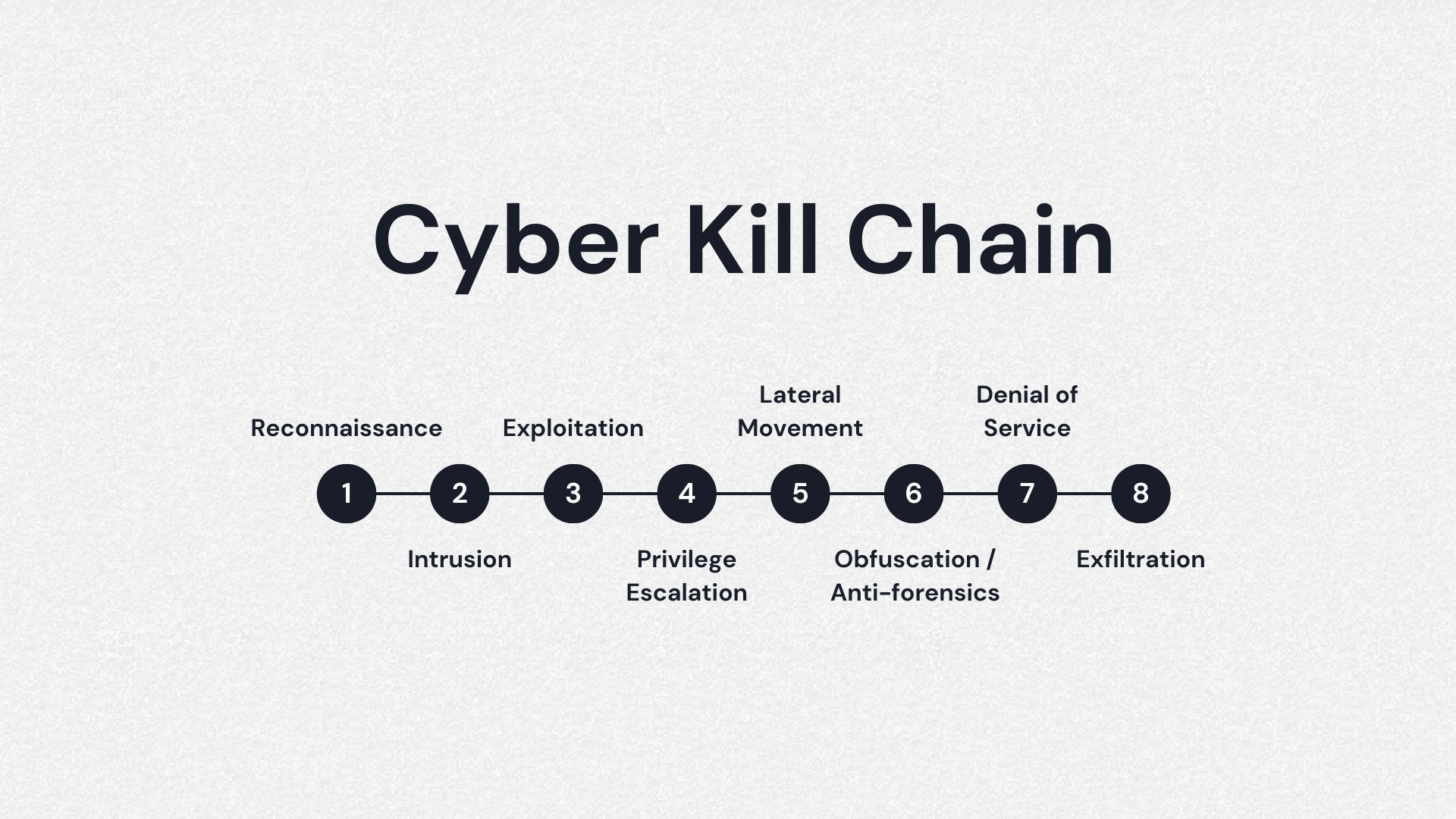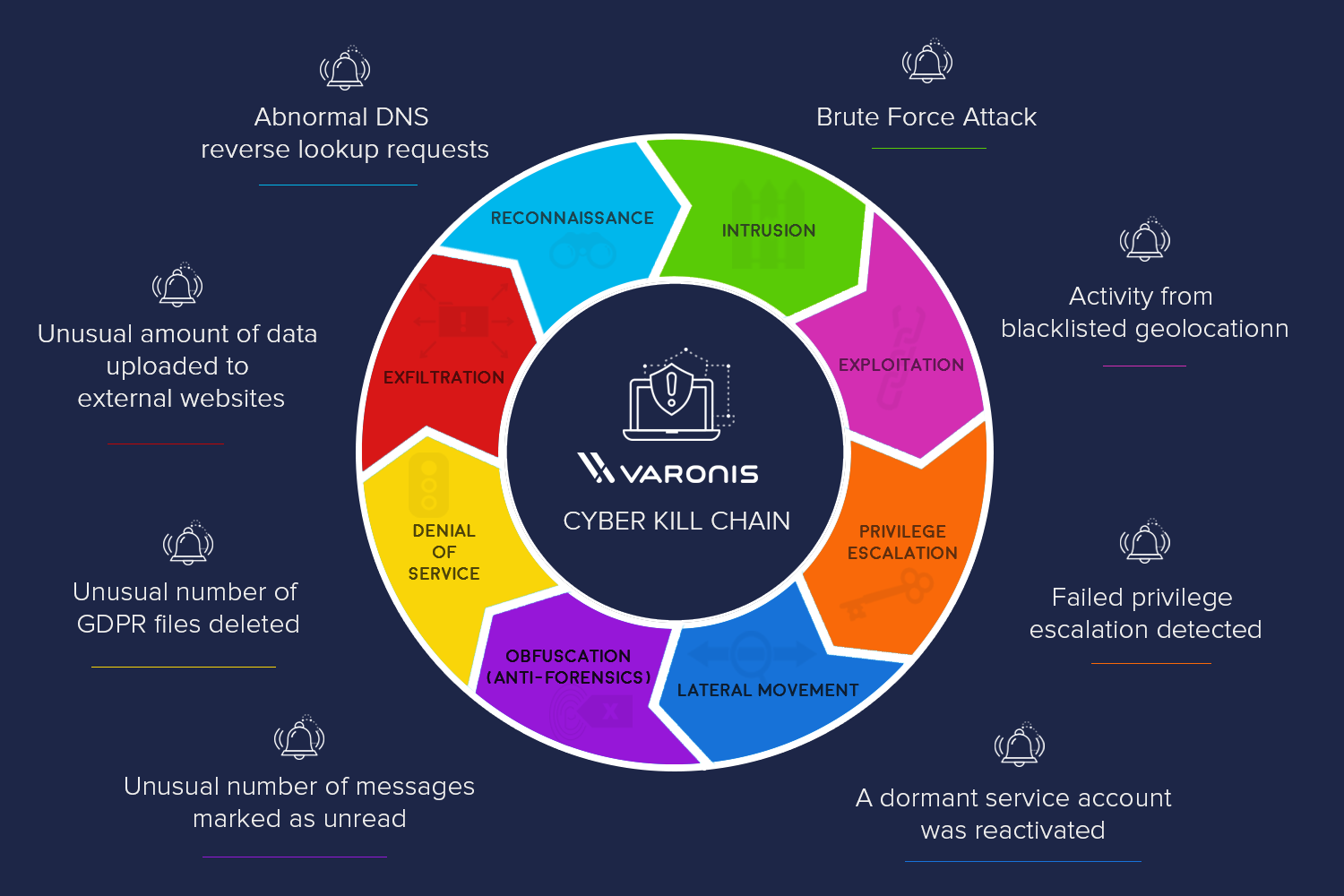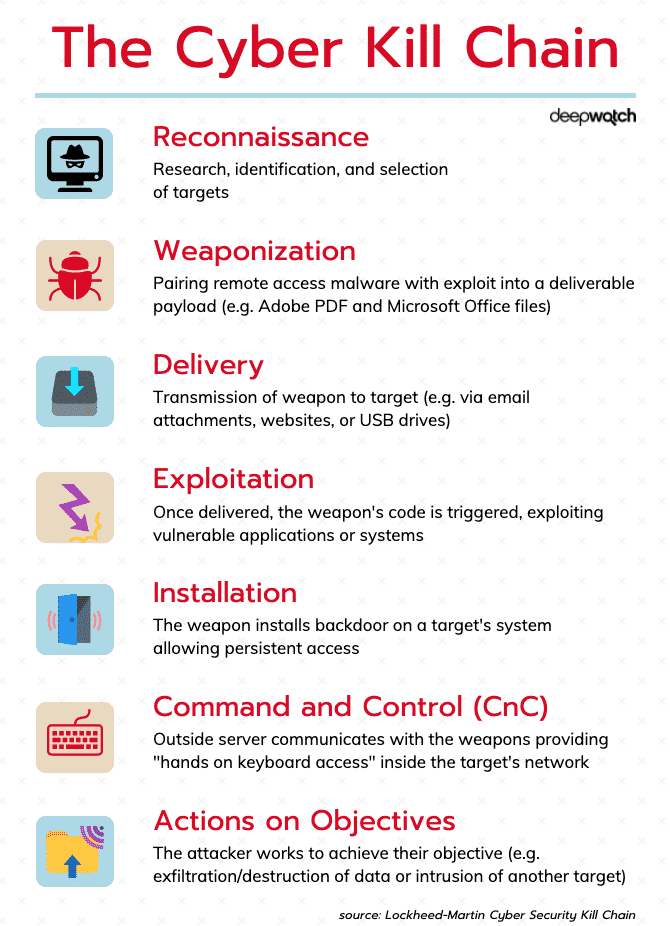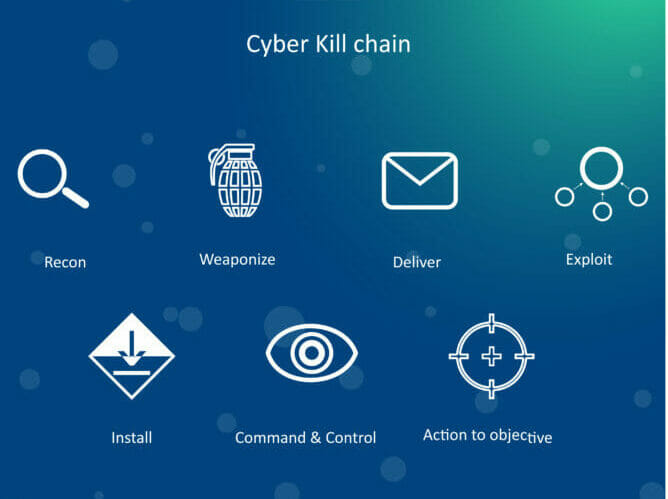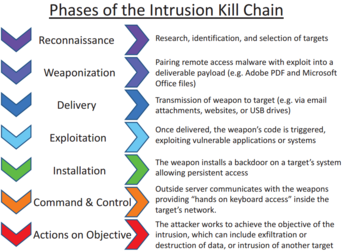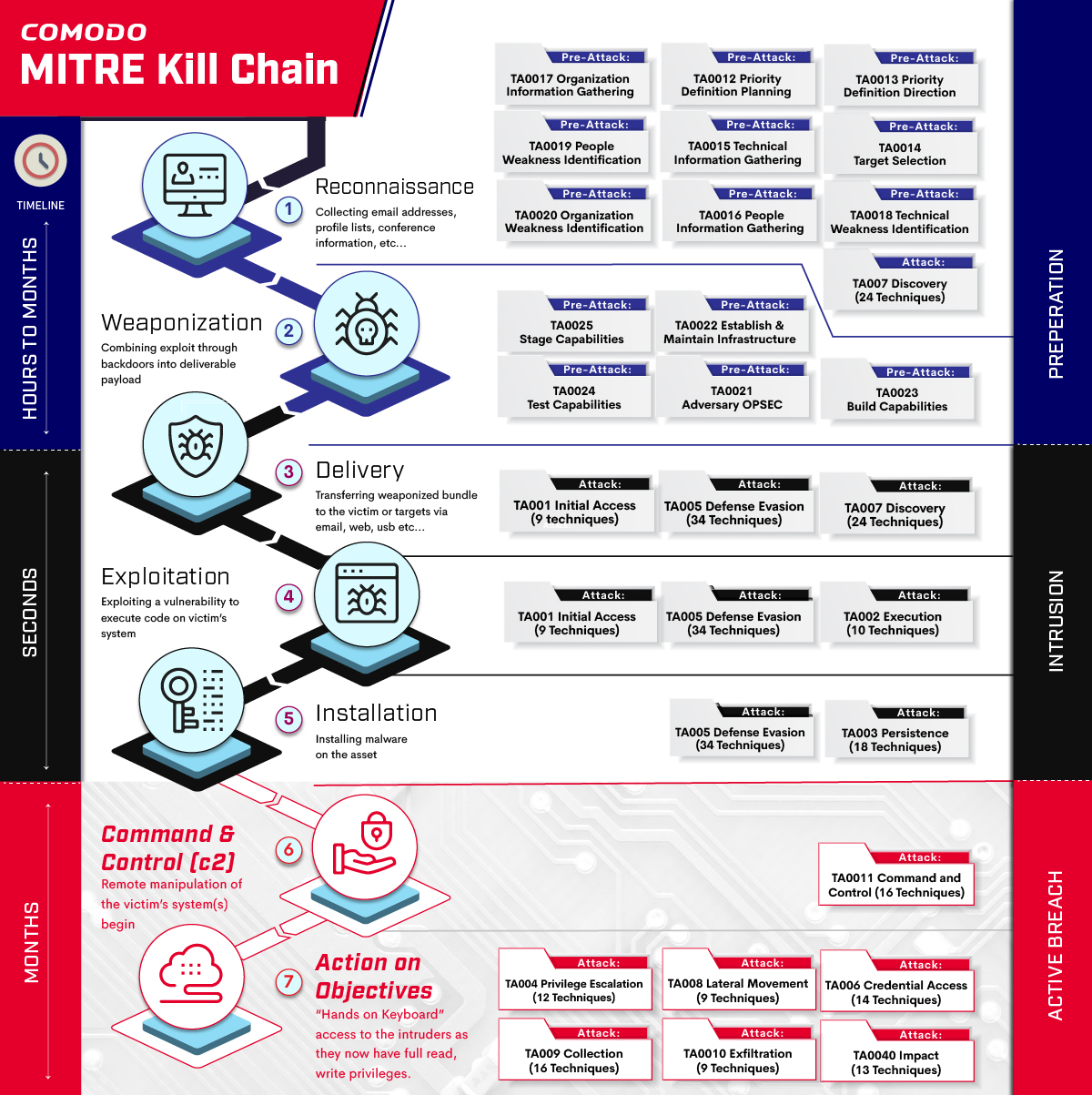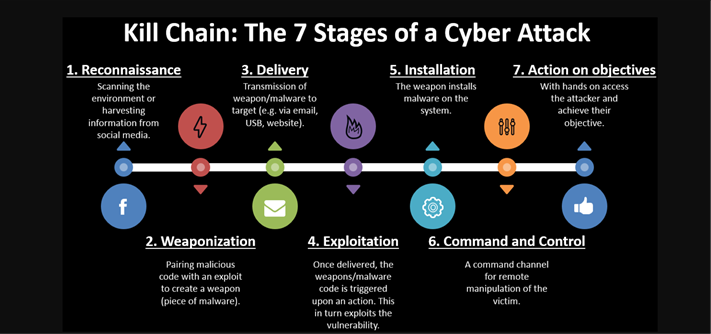
Applied Explanation of the “Cyber Kill Chain” Model as a Cyber Attack Methodology | by Ibrahim Akdağ| Ph.D. | Medium

DOD's Utilization of a Cyber Kill Chain Framework to Quantify Cyber Security Investments: Part 3 of the Key Cyber Defense Strategies Series - Government Technology Insider

View of Railway Defender Kill Chain to Predict and Detect Cyber-Attacks | Journal of Cyber Security and Mobility
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)